- Cisco Vpn No Internet Access Windows 10 Home Edition
- Cisco Vpn No Internet Access Windows 10 File
- Vpn Connected No Internet Access
- Cisco Vpn No Internet Access Windows 10 64-bit
This document is a guide for administrators and users while troubleshooting client VPN issues. Use this document to identify and resolve client VPN issues faster. This article also outlines troubleshooting methods for client VPNconnectivity issues, primarily for Windows-based clients, including a list of common errors as well as some common issues and solutions for accessing resources over client VPN. For configuring client VPN on OS devices, please refer to our Client VPN OS Configuration documentation.
- My Cisco Anyconnect VPN Client keeps on disconnecting after I changed my laptop and upgraded to windows 10. My internet connection is same and it was working fine on my previous laptop. In Device Manager under Network Adapter I see a warning sign on my Microsoft Wi-Fi Direct Virtual Adapter.
- Click “Test Program”. This will open the program. If the issue still persist, you may contact the Cisco support team for a software upgrade to work the program in Windows 10. Please click on the below link to go to the Cisco support website.
No Users Can Connect:
Is the MX online?
I joined a Cisco IPSEC VPN (based on Group Authentication). I had to install the VPN using some tricks since is not working anymore on Windows 10. The problem is that once connected in VPN internet is no working anymore. This is my route table. I have to setup a VPN for an employee but when I connect to the VPN it can't even find the server. I have setup the VPN connection on a Windows 10 machine, and I know it is a problem with only this PC as others can connect fine. I have used the powershell command to enable split tunneling but that only got me internet access on the PC.
Ensure your MX is online and accessible over the internet. You can verify internet connectivity using the Ping appliance button on the Tools tab of the appliance status page.
(Security & SD-WAN > Appliance status > Tools > Ping appliance)
Incorrect MX IP address is specified
Consider enabling Dynamic DNS and using the hostname (e.g. '.com') rather than the MX IP address for connecting to the VPN. You can find your MX hostname on the Security & SD-WAN >Appliance status page.
If you are using an IP address to connect, verify that you’re attempting to reach the MX at the correct IP address. You can verify the MX IP address by going to the Security & SD-WAN > Appliance status page in the dashboard.
If you have two uplink connections, when the uplink fails over from primary to secondary, the MX IP address may change, which would cause the MX VPN connection to no longer work if configured to use the primary MX IP address.
UpstreamNAT/firewall issueontheMX side
If your MX is behind a NAT device (e.g. an upstream router or ISP modem), the MX uplink IP will most likely have a private IP from 172.16.X.X or 192.168.X.X or 10.X.X.X subnet range. Ensure UDP traffic on ports 500 and 4500 is being forwarded to the private uplink IP address of the MX. Also, verify if there are any firewalls blocking UDP traffic on ports 500 or 4500.
Take a packet capture on the WAN interface of the MX and confirm that traffic from the public IP of the VPN client and UDP port 500 and 4500 traffic is reaching the MX.
Authentication issue
If you are receiving authentication errors, reverify the username, password, and shared secret. Try a different authentication method other than the one you are using, like Meraki Cloud Authentication, RADIUS, or Active Directory. Refer to this KB if you are unable to connect with any of the authentication methods.
Shared secret mismatch
If you are not sure what the shared secret is, retrieve it using Show secret on the dashboard Client VPN page. VPNs require the shared secret to match on the VPN server and client before tunnels can be established. Try changing your shared secret to eliminate the shared secret issue.
Encryption method
Client VPN uses the L2TP/IP protocol, with 3DES and SHA1 respectively as the encryption and hashing algorithms. As a best practice, the shared secret should not contain any special characters at the beginning or end.
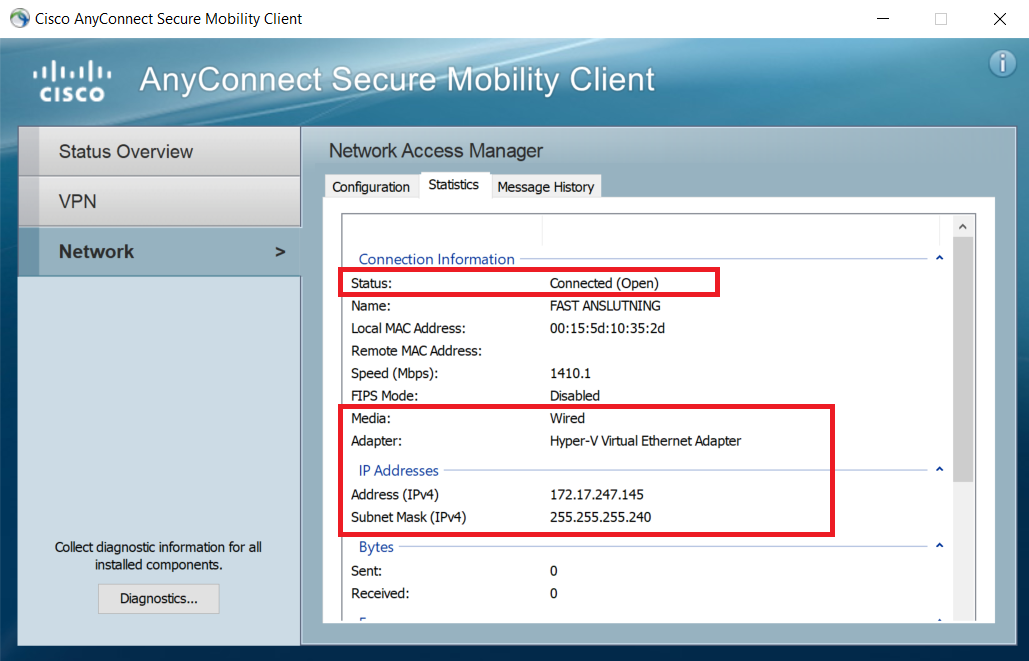
Some Users Can Connect:
Windows
VPN adaptor configurations/Windows update
A frequently seen issue is the VPN adaptor settings changing after a Windows update. If your VPN was working and has stopped connecting, check for bidirectional traffic between the VPN client and MX by taking a packet capture. If you see bidirectional traffic and are still unable to connect, review the VPN configuration settings. Please use this KB to verify or reconfigure your Windows VPN settings. Meraki is working on a long-term solution for this issue. You can also explore the Systems Manager Sentry option, which refreshes your VPN settings periodically to ensure your adaptor settings align with configurations on the VPN server.
Note: If your Windows device is failing to connect to the VPN, it is recommended that you verify the VPN configuration on your device to ensure it matches the Client VPN OS Configuration requirements.
Common Windows errors 789, 691, 809, 720, etc.
If a client VPN connection is failing to establish from a Windows device, but no error message appears on the screen, the Event Viewer can be used to find an error code associated with the failed connection attempt:
Step 1. Press the Windows key and type 'Event Viewer,' then click on Event Viewer in the search results.
Step 2. In Event Viewer, navigate to Windows Logs > Application.
Step 3. A client VPN connection failure should show up as an Error event type. Clicking on the event will show the associated error code.
Microsoft's knowledge base article lists error codes and their meanings however, some of the more frequently seen error codes are listed here:
Windows Error 789
Example event log entries:
This issue may also result in no event log messages if the client's traffic doesn't successfully reach the MX's WAN interface.
Possible causes and solutions:
- Incorrect secret key (preshared key in Windows)
Solution: Ensure that the shared secret is configured correctly on the client machine. It must match between the MX and the client. More information about setting the shared secret can be found in the links at the top of the page.
- Firewall blocking VPN traffic to MX
Solution: Ensure UDP ports 500 (IKE) and 4500 (IPsec NAT-T) are being forwarded to the MX and not blocked. If traffic cannot reach the MX on these ports, the connection will time out and fail.
- IKE and AuthIP IPsec keying modules disabled (Windows only)
Solution: This occurs most often when third-party VPN software has been installed and disables the IKEEXT service. This can be reenabled by navigating in Windows to Control Panel > Administrative Tools > Services. Find the service named 'IKE and AuthIP IPsec Keying Modules' and open it. Change the Startup type to 'Automatic.' If this automatically reverts to 'Disabled' or fails to start, it may be necessary to remove the third-party VPN software.
Windows Error 691
Example event log entries:
Possible causes and solutions:
- Invalid user credentials
Solution: Confirm user credentials are correct. When using Meraki authentication, usernames should be in email format (ex. user@example.com). When using AD or RADIUS authentication, be sure to enter the username in a format that will be recognized by the server, including the domain if needed (ex. DOMAINuser).
- User not authorized
Solution: If using Meraki authentication, ensure that the user has been authorized to connect to the VPN.
- No certificate on AD server
High sierra dmg. Solution: If using Active Directory authentication with Client VPN, make sure the AD server has a valid certificate for TLS.
- Incorrect DNS name resolution from the MX's upstream DNS server
Solution: If the MX is configured with an ISP DNS server, change this to a non-ISP public DNS server such as Google 8.8.8.8.
- Alternatively, this message can be caused when a mismatch of preshared secrets between a RADIUS server and MX results in bad encryption of the password. Test this by changing the preshared secret in dashboard and for the RADIUS client on the server to something simple, such as 'Meraki.' If the error disappears, verify the secret used is correct on both devices and simplify the password if needed.
Windows Error 809
If this error appears, the Event Log won't have any relevant logs, as the traffic doesn't reach the MX's WAN interface.
Possible causes and solutions:
- Client behind NAT devices
Solution: Modern Windows devices do not support L2TP/IPsec connections when the Windows computer or VPN server are located behind a NAT. If the Windows VPN client fails with Error 809 when trying to establish a VPN connection to an MX located behind a NAT, add the 'AssumeUDPEncapsulationContextOnSendRule' DWORD value to the Windows registry. This DWORD value allows Windows to establish security associations when both the VPN server and the Windows-based VPN client computer are behind NAT devices.
- For Windows XP:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesIPSec
RegValue: AssumeUDPEncapsulationContextOnSendRule
Type: DWORD
Value data: 2
Base: Decimal
- For Windows Vista, 7, 8, 10, and 2008 server:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesPolicyAgent
RegValue: AssumeUDPEncapsulationContextOnSendRule
Type: DWORD
Value data: 2
Base: Decimal
Note: that after creating this key you will need to reboot the machine. For more information, reference this Microsoft Support knowledge base article.
Note: Some third-party network programs can also cause Windows Error 809 to occur. SmartByte is one such program known to cause this issue. Disabling the program should resolve the issue and allow the VPN to connect.
Windows Error 720
If, when attempting to connect, the above message comes up, check the Windows Event Viewer for Error Code 720.
This most likely means that the client VPN subnet IP pool is exhausted. Check the Meraki dashboard Event Log for the event type VPN client address pool empty:
To address this, you will need a larger subnet size for client VPN users. For example, use 192.168.0.0/23 instead of 192.168.0.0/24. Note that one IP in the subnet is consumed for internal use by the MX security appliance, so a /24 subnet which provides 254 usable IP addresses will allow for 253 VPN clients to connect, assuming the MX model supports that many concurrent users. See the MX Sizing Principles guide for exact numbers.
SmartByte application
Another common issue with VPN connections from Windows devices is the SmartByte application. If it is installed, please try uninstalling it and reinitiating your VPN connection.
macOS
Not many client VPN connection issues are seen with macOS devices. If you do see this, try to connect on a different Mac device and OS version.
Mobile and IPv6
Mobile users usually have little or no trouble connecting. If you are having issues, double-check your configuration. Try resetting your network settings and reconfigure. See the Client VPN OS Configuration KB. If you are trying to connect over cellular, it could be an issue with your cellular provider. Try connecting via Wi-Fi.
Sometimes the event log will log the message, 'msg: unsupported ID type 5.' If the identification field value is 5 in the identification payload, this means the payload is carrying the ID type 'ID_IPV6_ADDR.' Meraki does not currently support ID type 5, so an error will appear for these ISAKMP messages. This message will appear for devices that do not have an IPv4 address assigned to them directly, and, as such, are reliant upon an IPv6 transition mechanism like NAT64 to reach the internet. Such devices will not be able to connect to our client VPN solution at this time.
Other possible issues and solutions
Firewall issue on client side: If UDP traffic on port 500 and 4500 is not reaching the MX, the chances are high that UDP traffic on those ports is being blocked by another firewall between the end client and the MX. You may have to check the firewall rules or access control lists between the client and MX. Try connecting from a client device using a different ISP.
Device issue: You could be running into an issue specific to the device. Try connecting with a different device to verify if it is a device-specific issue. Try resetting your network settings or reset the device if possible.
User account issue: If your account is not authorized to connect to VPN or your credentials are wrong, try resetting your password or connecting with a working set of credentials to further isolate the issue.
The MX is Not Receiving the Client VPN Connection Attempt
Look at the event log page, using the filter Event type include: All Non-Meraki/Client VPN. Check whether the client's request is listed. If there is no connection attempt going through to the MX, it is possible that the internet connection that the end user is on may have blocked VPN. If this is the case, you may need to check the access control and firewall settings upstream of the client.
If the event log is not clear, take a packet capture on the MX using the WAN interface or client VPN interface. Check whether there is any traffic seen when the client attempts to connect.
Can Connect to VPN but Cannot Access Resources
If you are connected to the VPN but cannot access resources, a common cause is due to subnet overlap between the local client network and the network the resource is in. If the local network you are on has the same IP address as the network you are trying to get to, your request will never make it through the tunnel. To validate this, test with the full tunneling option to see if it makes a difference.
Additionally, end users may report that they are unable to map network shares over the client VPN tunnel. This could be potentially caused by a layer 7 firewall rule configured to block file sharing. Check the layer 7 firewall rules under Security appliance >Configure > Firewall > Layer 7.
Also, check any group policies that are applied to the target resource to ensure file sharing is not blocked in the group policy.
Accessing resources over the tunnel via IP vs. DNS
If you are unable to access resources via domain name (DNS), try accessing via IP. If you succeed in accessing via IP, it could be a DNS issue. Try to resolve the DNS host name and confirm if the public IP of the MX is being returned. If you are unable to resolve the DNS host name, check the local DNS settings.
Note: It is possible to apply group policies to clients connected via client VPN. If a resource isn't pingable or a particular application isn't working, it would be a good idea to check the client details page to see if any group policies have been applied. For more help on assigning or removing group policies applied to a client, refer to the Creating and Applying Group Policies document.
Note: that Microsoft's Windows firewall typically blocks communication from unknown private subnets by default.
Resolving NetBIOS names over client VPN
Windows hosts utilize NetBIOS-based name resolution to locate Windows file and print shares located on other Windows hosts. A NetBIOS name syntax appears as 'MYCOMPUTER' and is normally seen in UNC paths such as MYCOMPUTERmyfileshare.
NetBIOS name resolution is a layer 2 broadcast-based name discovery protocol. Layer 2 broadcasts do not traverse layer 3 boundaries such as the client VPN interface on an MX.
WINS is a service that provides centralized name resolution of NetBIOS hostnames. NetBIOS clients register their hostnames on the WINS server and other NetBIOS clients query the WINS server to resolve NetBIOS names.
To allow hosts that utilize NetBIOS names to find network resources over client VPN, specify the IP address of a WINS server in the client VPN configuration. This is done using the WINS setting on the Security & SD-WAN > Configure > Client VPN page.
In the screenshot below, the specified WINS server is 192.168.1.100:
Connection is slow
If you are connected but your connection is slow, first identify if your connection is slow to everything over the tunnel or just for specific internal resources. If your connection is slow to an application but fast to other resources via the tunnel, then it’s most likely not a VPN issue.
You can also run speed tests if traffic is fully tunneled. VPN speeds depend on a lot of factors, including bandwidth on the MX and client side, number of clients connected to MX, number of VPN tunnels on the MX, etc.
Sometimes a user's endpoint utilizing the client VPN connection may have connection issues to LAN endpoints that have dual NICs. Often, LAN endpoints have both a WAN and a LAN NIC. If these devices are unpingable from an endpoint connected via client VPN, check the routes on the LAN endpoints. In Windows, open the command prompt and type the command 'route print'. In macOS, open up the terminal and type the command 'netstat -nr'. Check that there are gateways set for the LAN routes and not just the WAN.
Max Sessions per User Account
For security purposes, we limit each user's account to five (5) simultaneous VPN connections to an MX. If you need to change this number, please contact Cisco Meraki Support.
Client VPN connection issues can be effectively troubleshot by using packet captures. In this section, best practices and expected behavior in terms of what can be seen in a packet capture will be discussed, and common troubleshooting steps are explained.
Negotiation Process
For any client VPN connection, expect to follow the above process. If the process breaks down at any point, there are some specific things to look for at each step. To start, take a WAN packet capture (on the primary WAN) and follow the guide below.
Understanding the WAN Packet Capture
Filter the WAN pcap for the client’s public IP and ISAKMP/ESP, if necessary. Look for the ISAKMP “Next payload” field, which identifies the negotiation step. Start at the first “Security Association” from the client.
Troubleshooting Tips
If no ISAMKP traffic from the client is seen:
- Verify client is connecting to the primary MX WAN IP (VIP for warm spare)
- Verify inbound UDP 500 traffic is not being blocked/dropped upstream
- If the MX is behind a NAT, port forwarding may need to be configured on the upstream device for UDP ports 500 and 4500
- Some OS-specific behaviors may prevent the client machine from generating any traffic. Try to rule this out by testing another device type (e.g. a different OS or smart phone)
ISAKMP Phase 1
1. Security Association
The initiator sends a Security Association and the responder sends a Security Association response.
2. Key Exchange
The initiator sends a Key Exchange and the responder sends a Key Exchange response.
Troubleshooting Tips

Phase 1 uses UDP 500, phase 2 uses UDP 500 or UDP 4500 (NAT-T)
If the MX doesn’t respond to the client, verify:
The destination IP and MAC addresses (or VIP for warm spare) are correct
Port forwarding isn’t configured on the MX for port 500
Client isn’t trying to connect from behind the same MX
Client public IP doesn’t match any non-Meraki VPN peer IPs or another currently connected VPN client
Any extra configuration options manually applied to the MX that would override default client VPN settings
If both sides are continually sending Security Association, this may indicate port 500 traffic isn’t being received at the client
If one side is continually sending Key Exchange, this may indicate one of the following problems:
Incorrect preshared key
Port 4500 traffic to initiate phase 2 is being dropped/filtered (not reaching the client)
ISAKMP Phase 2
3. Identification
The initiator sends an Identification, and the responder sends an Identification response.
4. Hash
The initiator sends a Hash, and the responder sends a Hash response.
Troubleshooting Tips
- Phase 2 uses UDP 4500 (NAT-T) or sometimes UDP 500
If both sides are continually sending phase 2 packets, this may indicate one of the following problems:
Incorrect encryption/authentication settings
Incorrect subnet definition (site-to-site only)
The client may need to verify their VPN settings. For additional information on specific OS configuration, please follow this article on Client VPN OS Configuration.
Windows clients may need to install the registry fix as mentioned above.
ESP
If bidirectional ESP traffic is seen, the tunnel is up.
User authentication happens at this step
The WAN packet capture will no longer be helpful, since everything is encrypted past this point
Verify if the authentication is successful between the MX and the authentication server
Troubleshooting Tips
For Meraki Cloud authentication, verify:
The MX WAN port can resolve meraki.com via DNS, and all required cloud connections are allowed on upstream equipment; for additional explanation of what Meraki requires for cloud communication, please reference the documentation on upstream rules for cloud connectivity
- The account is 'Authorized for client VPN' in dashboard and the password is correct
Cisco Vpn No Internet Access Windows 10 Home Edition
- For RADIUS authentication, verify:
- RADIUS authentication packets sent between MX and server must result in ACCESS-ACCEPT for successful connection
- RADIUS server event log, which is explained in the RADIUS Issue Resolution Guide
- For Active Directory authentication, verify:
- Active Directory packets sent between MX and server show a successful TLS connection
- Active Directory server event log
- For all authentication types:
If no authentication logs or packets are seen, the client may not be sending credentials
The client may need to verify their VPN settings
If the problem exists for only one client, troubleshooting may be required at the client machine (e.g. reboot, check for conflicting software)
- If authentication is successful but client still fails to connect, ensure the IP pool for the client VPN subnet is not exhausted
Verifying a Successful Connection
There are three primary ways to determine if the client VPN connection is successfully connected to an MX:
- Check the device for connection status using common network utilities (this will vary depending on the operating system being used). The event log contains entries each time a client connects or disconnects from client VPN. These logs can be viewed from Monitor > Event log. Deselect all event categories except VPN, then click on the Search button. Client VPN logs will have one of two event types: VPN client connected or VPN client disconnected. Here is an example set of log messages that show a client connecting and then disconnecting from client VPN:
- The client list can also be used to see if a client is currently connected to client VPN. Browse to Monitor > Clients in the dashboard. Add an additional column by clicking on the '+' button and select MAC address. Clients can then be filtered by 'N/A (client VPN)' as the MAC address.
Common inquiries
- Client VPN monitoring: to monitor client VPN users, filter by 'Client VPN' & 'Connected' on dashboard > Network-wide > Clients and search the drop-down menu
- Additional licensing is not required for client VPN. Client VPN is included in Enterprise, Advanced Security, and Secure SD-WAN MX licensing.
Note
Intune may support more settings than the settings listed in this article. Not all settings are documented, and won’t be documented. To see the settings you can configure, create a device configuration profile, and select Settings Catalog. For more information, see Settings catalog.
You can add and configure VPN connections for devices using Microsoft Intune. This article describes some of the settings and features you can configure when creating virtual private networks (VPNs). These VPN settings are used in device configuration profiles, and then pushed or deployed to devices.
As part of your mobile device management (MDM) solution, use these settings to allow or disable features, including using a specific VPN vendor, enabling always on, using DNS, adding a proxy, and more.

These settings apply to devices running:
- Windows 10
- Windows Holographic for Business
Before you begin
Deploy your VPN app, and create a Windows 10 VPN device configuration profile. The available settings depend on the VPN client you choose. Some settings are only available for specific VPN clients.
These settings use the VPNv2 CSP.
Base VPN
Connection name: Enter a name for this connection. End users see this name when they browse their device for the list of available VPN connections.
Servers: Add one or more VPN servers that devices connect to. When you add a server, you enter the following information:
- Description: Enter a descriptive name for the server, such as Contoso VPN server.
- IP address or FQDN: Enter the IP address or fully qualified domain name (FQDN) of the VPN server that devices connect to, such as 192.168.1.1 or vpn.contoso.com.
- Default server: Enables this server as the default server that devices use to establish the connection. Set only one server as the default.
- Import: Browse to a comma-separated file that includes a list of servers in the format: description, IP address or FQDN, Default server. Choose OK to import these servers into the Servers list.
- Export: Exports the list of servers to a comma-separated-values (csv) file.
Register IP addresses with internal DNS: Select Enable to configure the Windows 10 VPN profile to dynamically register the IP addresses assigned to the VPN interface with the internal DNS. Select Disable to not dynamically register the IP addresses.
Connection type: Select the VPN connection type from the following list of vendors:
- Cisco AnyConnect
- Pulse Secure
- F5 Access
- SonicWall Mobile Connect
- Check Point Capsule VPN
- Citrix
- Palo Alto Networks GlobalProtect
- Automatic
- IKEv2
- L2TP
- PPTP
When you choose a VPN connection type, you may also be asked for the following settings:
Always On: Enable automatically connects to the VPN connection when the following events happen:
- Users sign into their devices
- The network on the device changes
- The screen on the device turns back on after being turned off
To use device tunnel connections, such as IKEv2, Enable this setting.
Authentication method: Select how you want users to authenticate to the VPN server. Your options:
Username and password: Require users to enter their domain username and password to authenticate, such as
user@contoso.com, orcontosouser.Certificates: Select an existing user client certificate profile to authenticate the user. This option provides enhanced features, such as zero-touch experience, on-demand VPN, and per-app VPN.
To create certificate profiles in Intune, see Use certificates for authentication.
Derived credential: Use a certificate that's derived from a user's smart card. If no derived credential issuer is configured, Intune prompts you to add one. For more information, see Use derived credentials in Intune.
Machine certificates (IKEv2 only): Select an existing device client certificate profile to authenticate the device.
If you use device tunnel connections, you must select this option.
To create certificate profiles in Intune, see Use certificates for authentication.
EAP (IKEv2 only): Select an existing Extensible Authentication Protocol (EAP) client certificate profile to authenticate. Enter the authentication parameters in the EAP XML setting.
Remember credentials at each logon: Choose to cache the authentication credentials.
Custom XML: Enter any custom XML commands that configure the VPN connection.
EAP XML: Enter any EAP XML commands that configure the VPN connection. For more information, see EAP configuration.
Device tunnel (IKEv2 only): Enable connects the device to the VPN automatically without any user interaction or sign in. This setting applies to PCs joined to Azure Active Directory (AD).
To use this feature, the following are required:
- Connection type setting is set to IKEv2.
- Always On setting is set to Enable.
- Authentication method setting is set to Machine certificates.
Only assign one profile per device with Device Tunnel enabled.
IKE Security Association Parameters (IKEv2 only): These cryptography settings are used during IKE security association negotiations (also known as
main modeorphase 1) for IKEv2 connections. These settings must match the VPN server settings. If the settings don't match, the VPN profile won't connect.Encryption algorithm: Select the encryption algorithm used on the VPN server. For example, if your VPN server uses AES 128 bit, then select AES-128 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Integrity check algorithm: Select the integrity algorithm used on the VPN server. For example, if your VPN server uses SHA1-96, then select SHA1-96 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Diffie-Hellman group: Select the Diffie-Hellman computation group used on the VPN server. For example, if your VPN server uses Group2 (1024 bits), then select 2 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Child Security Association Parameters (IKEv2 only): These cryptography settings are used during child security association negotiations (also known as
quick modeorphase 2) for IKEv2 connections. These settings must match the VPN server settings. If the settings don't match, the VPN profile won't connect.Cipher transform algorithm: Select the algorithm used on the VPN server. For example, if your VPN server uses AES-CBC 128 bit, then select CBC-AES-128 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Authentication transform algorithm: Select the algorithm used on the VPN server. For example, if your VPN server uses AES-GCM 128 bit, then select GCM-AES-128 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Perfect forward secrecy (PFS) group: Select the Diffie-Hellman computation group used for perfect forward secrecy (PFS) on the VPN server. For example, if your VPN server uses Group2 (1024 bits), then select 2 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Pulse Secure example
F5 Edge Client example
SonicWALL Mobile Connect example
Login group or domain: This property can't be set in the VPN profile. Instead, Mobile Connect parses this value when the user name and domain are entered in the username@domain or DOMAINusername formats.
Example:
CheckPoint Mobile VPN example
Writing custom XML
For more information about writing custom XML commands, see each manufacturer's VPN documentation.
For more information about creating custom EAP XML, see EAP configuration.
Apps and Traffic Rules
Cisco Vpn No Internet Access Windows 10 File
Associate WIP or apps with this VPN: Enable this setting if you only want some apps to use the VPN connection. Your options:
- Associate a WIP with this connection: Enter a WIP domain for this connection
- Associate apps with this connection: You can Restrict VPN connection to these apps, and then add Associated Apps. The apps you enter automatically use the VPN connection. The type of app determines the app identifier. For a universal app, enter the package family name. For a desktop app, enter the file path of the app.
Important
We recommend that you secure all app lists created for per-app VPNs. If an unauthorized user changes this list, and you import it into the per-app VPN app list, then you potentially authorize VPN access to apps that shouldn't have access. One way you can secure app lists is using an access control list (ACL).
Network traffic rules for this VPN connection: Select the protocols, and the local & remote port and address ranges, are enabled for the VPN connection. If you don't create a network traffic rule, then all protocols, ports, and address ranges are enabled. After you create a rule, the VPN connection uses only the protocols, ports, and address ranges that you enter in that rule.
Conditional Access
Conditional Access for this VPN connection: Enables device compliance flow from the client. When enabled, the VPN client communicates with Azure Active Directory (AD) to get a certificate to use for authentication. The VPN should be set up to use certificate authentication, and the VPN server must trust the server returned by Azure AD.
Single sign-on (SSO) with alternate certificate: For device compliance, use a certificate different from the VPN authentication certificate for Kerberos authentication. Enter the certificate with the following settings:
- Name: Name for extended key usage (EKU)
- Object Identifier: Object identifier for EKU
- Issuer hash: Thumbprint for SSO certificate
Vpn Connected No Internet Access
DNS Settings
DNS suffix search list: In DNS suffixes, enter a DNS suffix, and Add. You can add many suffixes.
When using DNS suffixes, you can search for a network resource using its short name, instead of the fully qualified domain name (FQDN). When searching using the short name, the suffix is automatically determined by the DNS server. For example,
utah.contoso.comis in the DNS suffix list. You pingDEV-comp. In this scenario, it resolves toDEV-comp.utah.contoso.com.DNS suffixes are resolved in the order listed, and the order can be changed. For example,
colorado.contoso.comandutah.contoso.comare in the DNS suffix list, and both have a resource calledDEV-comp. Sincecolorado.contoso.comis first in the list, it resolves asDEV-comp.colorado.contoso.com.To change the order, select the dots to the left of the DNS suffix, and then drag the suffix to the top:
Name Resolution Policy table (NRPT) rules: Name Resolution Policy table (NRPT) rules define how DNS resolves names when connected to the VPN. After the VPN connection is established, you choose which DNS servers the VPN connection uses.
You can add rules to the table that include the domain, DNS server, proxy, and other details to resolve the domain you enter. The VPN connection uses these rules when users connect to the domains you enter.
Select Add to add a new rule. For each server, enter:
- Domain: Enter the fully qualified domain name (FQDN) or a DNS suffix to apply the rule. You can also enter a period (.) at the beginning for a DNS suffix. For example, enter
contoso.comor.allcontososubdomains.com. - DNS servers: Enter the IP address or DNS server that resolves the domain. For example, enter
10.0.0.3orvpn.contoso.com. - Proxy: Enter the web proxy server that resolves the domain. For example, enter
http://proxy.com. - Automatically connect: When Enabled, the device automatically connects to the VPN when a device connects to a domain you enter, such as
contoso.com. When Not configured (default), the device doesn't automatically connect to the VPN - Persistent: When set to Enabled, the rule stays in the Name Resolution Policy table (NRPT) until the rule is manually removed from the device, even after the VPN disconnects. When set to Not configured (default), NRPT rules in the VPN profile are removed from the device when the VPN disconnects.
- Domain: Enter the fully qualified domain name (FQDN) or a DNS suffix to apply the rule. You can also enter a period (.) at the beginning for a DNS suffix. For example, enter
Cisco Vpn No Internet Access Windows 10 64-bit
Proxy
- Automatic configuration script: Use a file to configure the proxy server. Enter the proxy server URL that includes the configuration file. For example, enter
http://proxy.contoso.com/pac. - Address: Enter the IP address or fully qualified host name of the proxy server. For example, enter
10.0.0.3orvpn.contoso.com. - Port number: Enter the port number used by your proxy server. For example, enter
8080. - Bypass proxy for local addresses: This setting applies if your VPN server requires a proxy server for the connection. If you don't want to use a proxy server for local addresses, then choose Enable.
Split Tunneling
- Split tunneling: Enable or Disable to let devices decide which connection to use depending on the traffic. For example, a user in a hotel uses the VPN connection to access work files, but uses the hotel's standard network for regular web browsing.
- Split tunneling routes for this VPN connection: Add optional routes for third-party VPN providers. Enter a destination prefix, and a prefix size for each connection.
Trusted Network Detection
Trusted network DNS suffixes: When users are already connected to a trusted network, you can prevent devices from automatically connecting to other VPN connections.
In DNS suffixes, enter a DNS suffix that you want to trust, such as contoso.com, and select Add. You can add as many suffixes as you want.
If a user is connected to a DNS suffix in the list, then the user won't automatically connect to another VPN connection. The user continues to use the trusted list of DNS suffixes you enter. The trusted network is still used, even if any autotriggers are set.
For example, if the user is already connected to a trusted DNS suffix, then the following autotriggers are ignored. Specifically, the DNS suffixes in the list cancel all other connection autotriggers, including:
- Always on
- App-based trigger
- DNS autotrigger
Next steps
The profile is created, but may not be doing anything yet. Be sure to assign the profile, and monitor its status.
Configure VPN settings on Android, iOS/iPadOS, and macOS devices.




